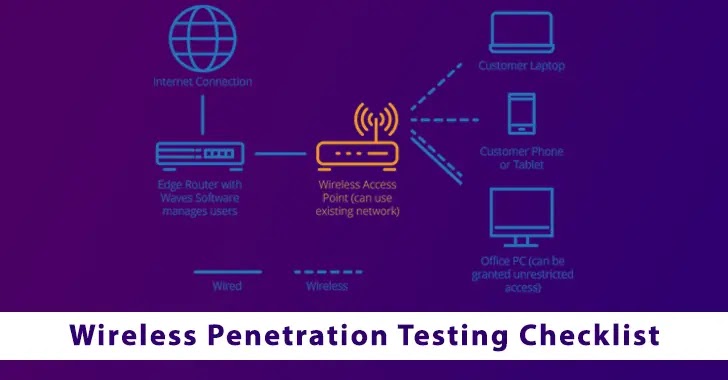
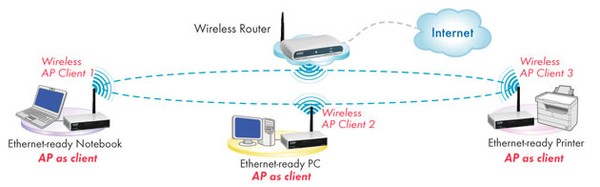
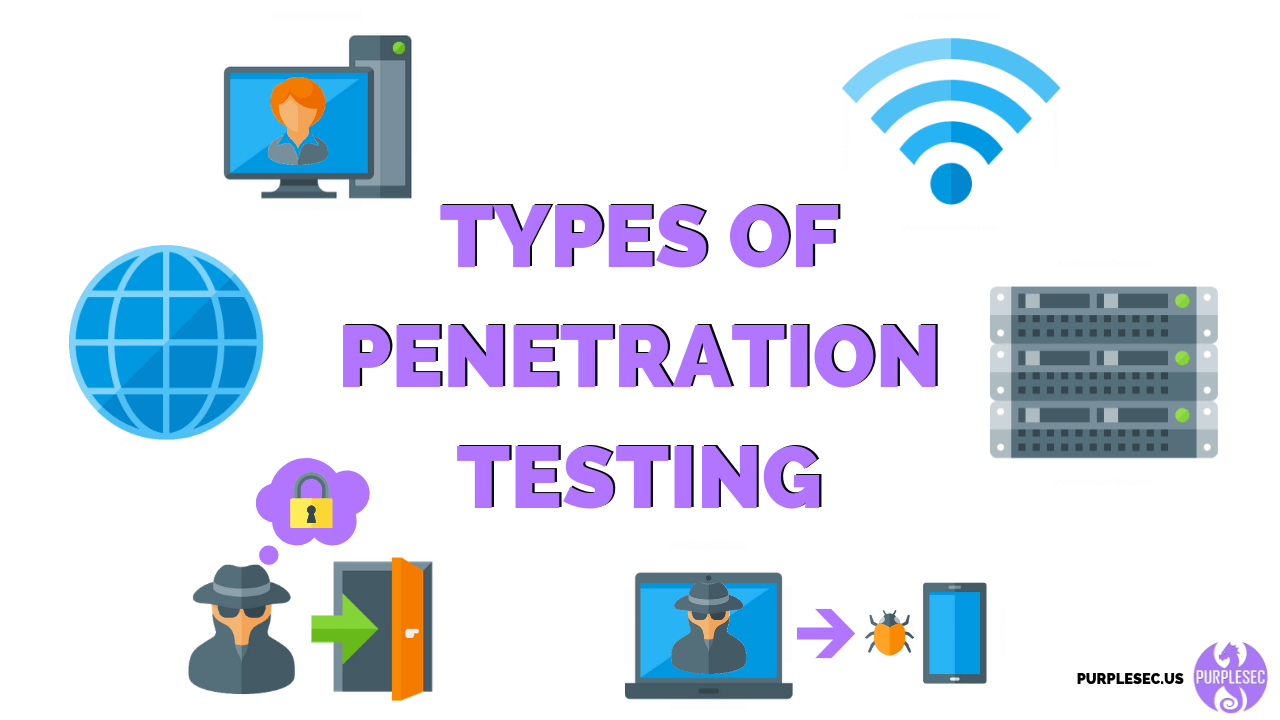
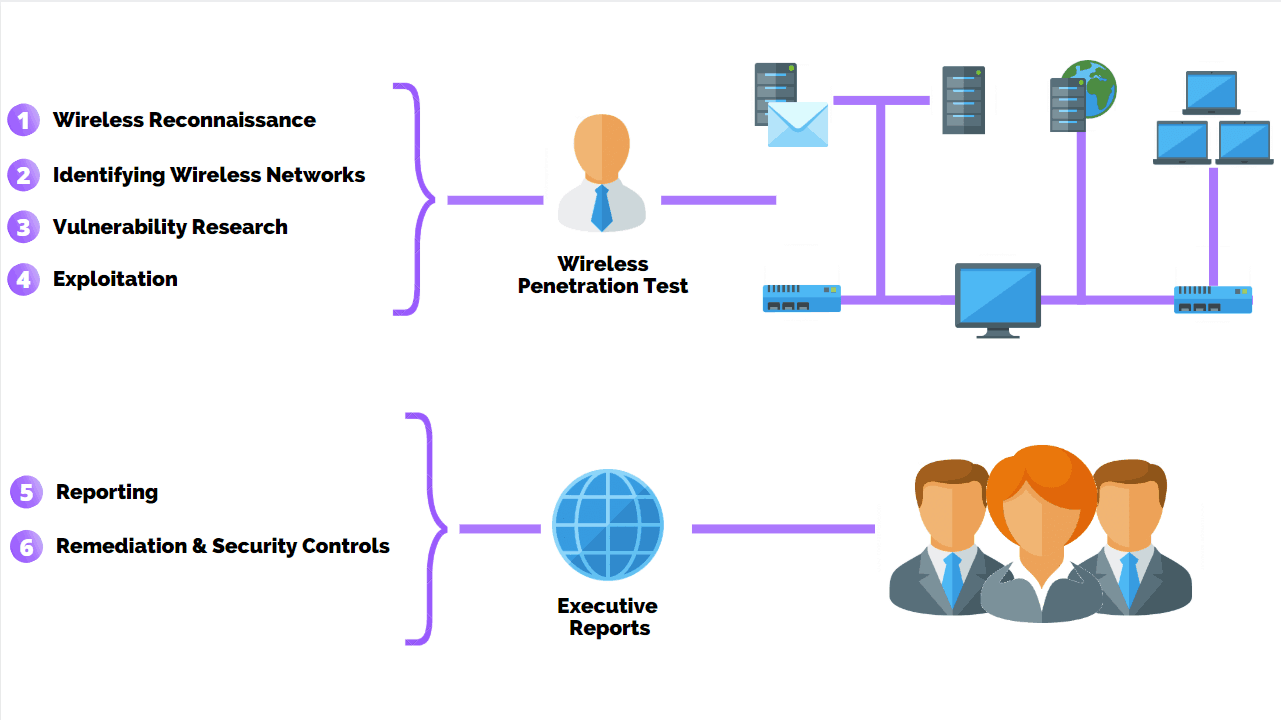
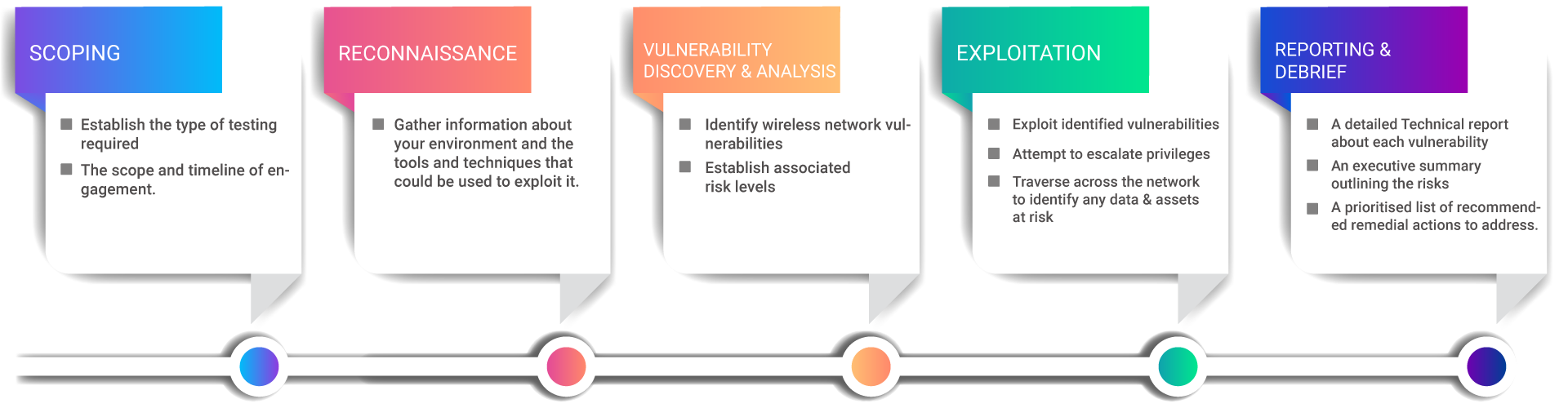
Wireless Network Penetration Testing | Managed IT Services and Cyber Security Services Company - Teceze

Kali Linux Wireless Penetration Testing: Beginner's Guide: Learn to penetrate Wi-Fi and wireless networks to secure your system from vulnerabilities: Ramachandran, Vivek, Buchanan, Cameron: 9781783280414: Amazon.com: Books